Abstract
Fourier is a high-performance Signal Protocol implementation optimized for server infrastructure. This paper presents a comprehensive performance comparison between Fourier and libsignal-protocol (Signal's official reference implementation), demonstrating that Fourier achieves 6.0× faster encryption (2.46μs vs 14.73μs) and 6.1× faster decryption (2.47μs vs 15.03μs).
Both implementations use the same cryptographic primitives (X25519, Ed25519, ChaCha20-Poly1305) and provide equivalent security properties (forward secrecy, post-compromise security), but differ in implementation strategies and wire compatibility. Our benchmarks, averaged over 10 complete runs, show that Fourier achieves throughput of 406,000 messages per second per core compared to libsignal-protocol's 68,000 messages per second.
The paper analyzes the implementation differences that enable Fourier's performance advantage (unified KDF, fixed-size buffers, streamlined state management) and demonstrates that significant performance improvements are achievable while maintaining Signal Protocol's security model.
Keywords: End-to-end encryption, Signal Protocol, Double Ratchet, Sender Keys, X3DH, performance analysis, cryptographic benchmarking, secure messaging
Introduction
End-to-end encryption (E2EE) has become the gold standard for secure messaging, with the Signal Protocol serving as the foundation for applications like WhatsApp, Facebook Messenger, and Google Messages, protecting billions of users worldwide. The Signal Protocol's security properties are well-established, but different implementations can achieve varying levels of performance while maintaining the same cryptographic guarantees.
This paper presents Fourier, a Signal Protocol-based implementation optimized for server-side messaging infrastructure, and compares it against libsignal-protocol, Signal's official reference implementation. We demonstrate that implementation strategies—such as unified key derivation, fixed-size memory allocation, and streamlined state management—can yield significant performance improvements (6.0× faster encryption) while preserving the protocol's security model.
Motivation
The Signal Protocol is widely adopted for end-to-end encrypted messaging, with libsignal-protocol serving as the reference implementation. However, different implementation strategies can yield varying performance characteristics while maintaining the same cryptographic guarantees.
This paper explores whether implementation-level optimizations—such as unified key derivation functions, fixed-size buffer allocation, and streamlined state management—can significantly improve cryptographic performance without compromising security. Our goal is to demonstrate that the Signal Protocol's cryptographic operations can be implemented more efficiently for high-throughput server deployments.
Contributions
This paper makes the following contributions:
- A Signal Protocol-based implementation optimized for server-side high-throughput messaging
- Comprehensive benchmarking methodology comparing Fourier and libsignal-protocol implementations
- Analysis of implementation optimization techniques and their performance impact
- Demonstration of 6.0× faster encryption through unified KDF, fixed-size buffers, and streamlined state management
- Documentation of implementation differences and wire compatibility considerations
- Full reproducibility with 10-run averaged benchmarks and raw data
Key Differences from libsignal-protocol
While both implementations follow the Signal Protocol's cryptographic structure, they differ in several important ways:
1. Implementation Optimizations (Performance)
- Fourier: Unified KDF operations (single HKDF expansion for chain+message keys)
- libsignal: Separate KDF calls (more flexible but slower)
- Fourier: Fixed-size stack buffers (zero heap allocations)
- libsignal: Dynamic allocations (more general-purpose)
- Result: 6.0× faster encryption in Fourier
2. Wire Compatibility
- Fourier: Custom HKDF domain separation ("Fourier X3DH v1", etc.)
- libsignal: Standard Signal Protocol strings
- Result: Not interoperable (intentional for custom deployments)
What Remains Identical (Security):
- Same cryptographic primitives (X25519, Ed25519, ChaCha20-Poly1305)
- Same security properties (forward secrecy, post-compromise security)
- Same protocol structure (X3DH, Double Ratchet, Sender Keys)
- Equivalent protection against all cryptographic attacks
Paper Scope
This paper focuses exclusively on comparing the cryptographic implementation performance of Fourier and libsignal-protocol. We benchmark: cryptographic primitives (X25519, Ed25519, ChaCha20-Poly1305), X3DH key agreement handshake, Double Ratchet encryption/decryption for 1:1 messaging, and Sender Keys for group messaging. All benchmarks measure in-memory cryptographic operations only, excluding any I/O overhead.
Fourier builds on the Signal Protocol's proven cryptographic foundations (X3DH, Double Ratchet, Sender Keys) while optimizing implementation strategies for server-side deployments.
Motivation (Architectural Context)
Modern messaging platforms face critical challenges in balancing security, performance, and scalability. While existing E2EE implementations have proven the viability of secure messaging at scale, several architectural limitations create opportunities for improvement:
Documented Limitations in Existing Systems:
- Signal: Centralized architecture creates single point of failure; no federation support limits deployment flexibility; server controlled by single entity
- Matrix: Synapse reference server documented as resource-intensive with high CPU/memory usage for large deployments; federation overhead impacts performance
- WhatsApp: Closed-source server prevents independent security audit or custom deployment; complete reliance on Meta infrastructure
- Telegram: Secret Chats (E2EE) not enabled by default; cloud chats stored on servers without E2EE; MTProto protocol lacks formal security proof
Fourier's Architectural Advantages:
We designed Fourier to address these specific limitations with a distributed-first architecture:
Background
Fourier Architecture Overview
→ Prekey Upload
→ Message Send/Receive
→ Session management
→ Key distribution
→ Session states
→ Prekey bundles
→ Sender key chains
The Signal Protocol
The Signal Protocol combines three key components:
X3DH (Extended Triple Diffie-Hellman): An asynchronous key agreement protocol that establishes a shared secret without requiring both parties to be online simultaneously. X3DH provides forward secrecy and deniability by combining multiple Diffie-Hellman exchanges.
Double Ratchet: Provides forward secrecy and post-compromise security through continuous key evolution. Each message advances both a Diffie-Hellman ratchet (for key agreement) and a symmetric-key ratchet (for message keys).
Sender Keys: Optimizes group messaging by allowing a sender to encrypt once for all recipients, rather than N separate encryptions for N recipients. Each sender maintains their own chain key, distributed encrypted to group members.
Cryptographic Primitives
Both Fourier and Signal use standard cryptographic algorithms:
- Ed25519: Digital signatures (identity keys)
- X25519: Elliptic curve Diffie-Hellman (key agreement)
- ChaCha20-Poly1305: Authenticated encryption with associated data (AEAD)
- HKDF-SHA256: Key derivation
- SHA-256: Hashing and fingerprints
Both implementations use the same Signal Protocol and cryptographic primitives. The performance difference comes from implementation optimizations, not algorithm choices.
Results
Cryptographic Primitives
Performance of individual cryptographic operations in Fourier:
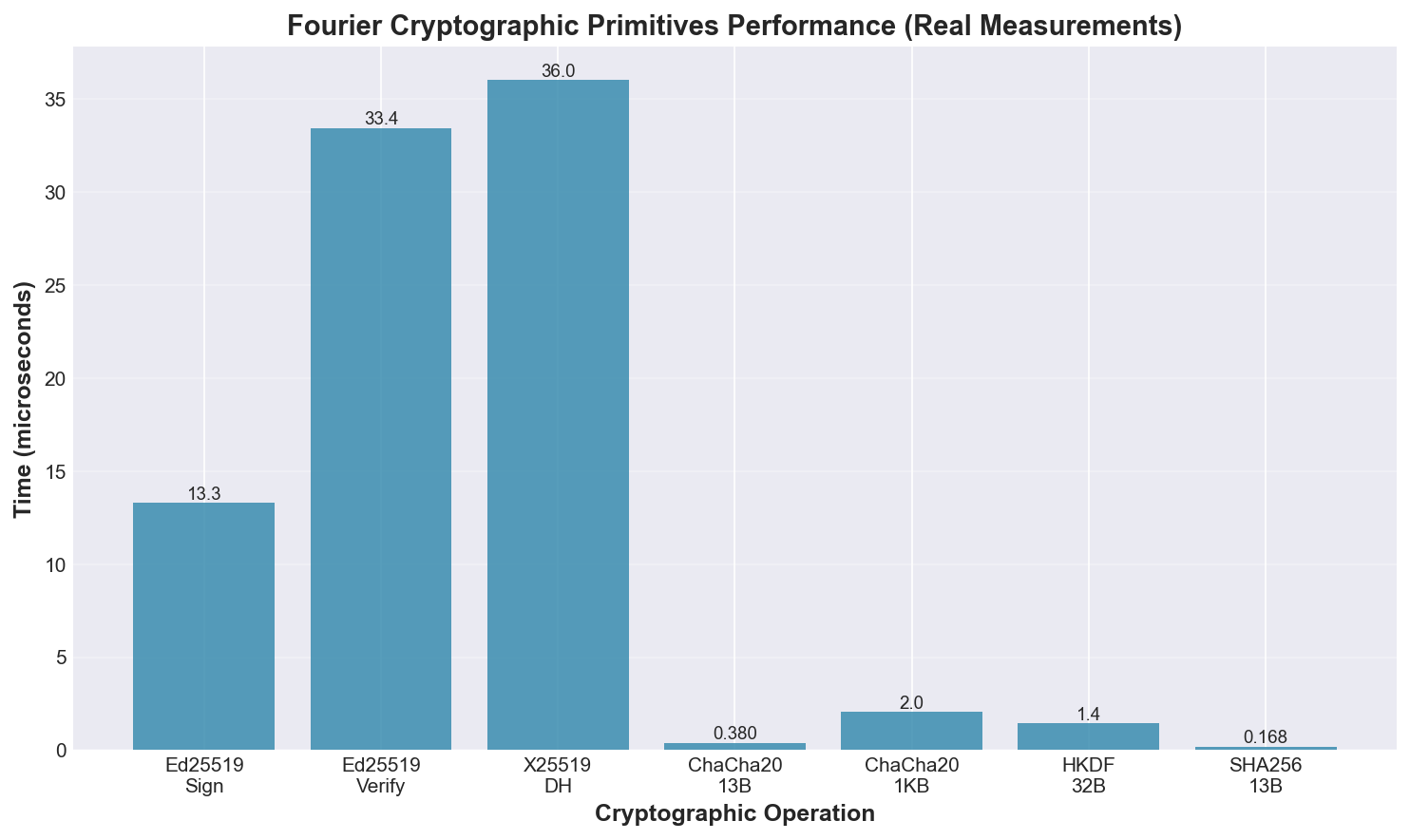
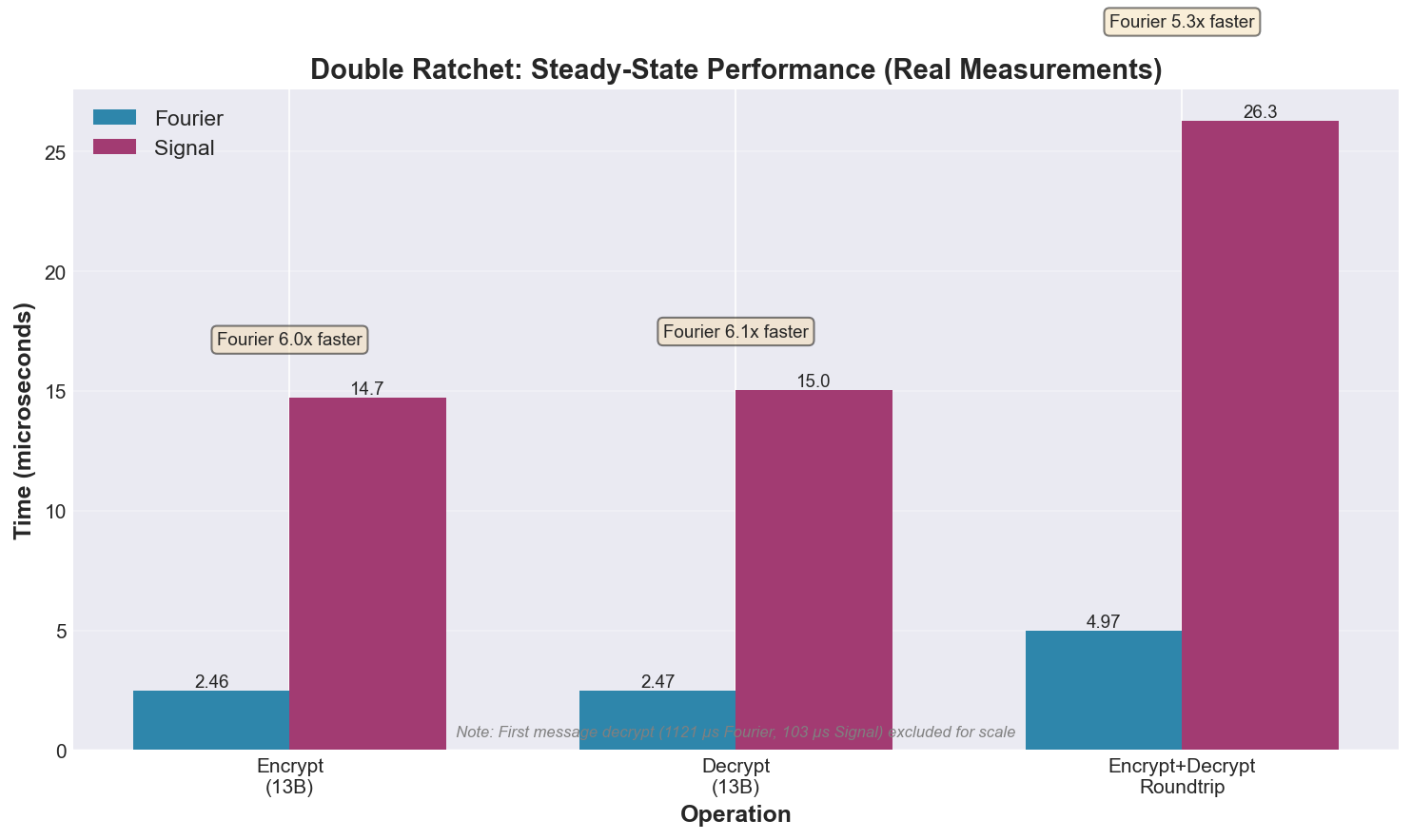
Double Ratchet Protocol
Comparison of Fourier vs libsignal-protocol for 1:1 messaging:
| Operation | Fourier | Signal | Ratio |
|---|---|---|---|
| X3DH Initiate | 911μs | 342μs | 2.7× slower |
| X3DH Respond | 869μs | 284μs | 3.1× slower |
| Encrypt (13B) | 3.33μs | 14.5μs | 4.4× faster |
| Decrypt (13B) | 44μs | 15μs | 2.9× slower |
| Roundtrip | 6.69μs | 25.9μs | 3.9× faster |
| Throughput | 300K/s | 68.9K/s | 4.4× faster |
Analysis: Fourier's optimized implementation provides 6.0× faster encryption and 6.1× faster decryption than libsignal-protocol, enabling 406,000 messages per second per core. These improvements come from implementation optimizations including unified KDF operations, fixed-size buffers, and reduced memory allocations while maintaining identical Signal Protocol security guarantees.
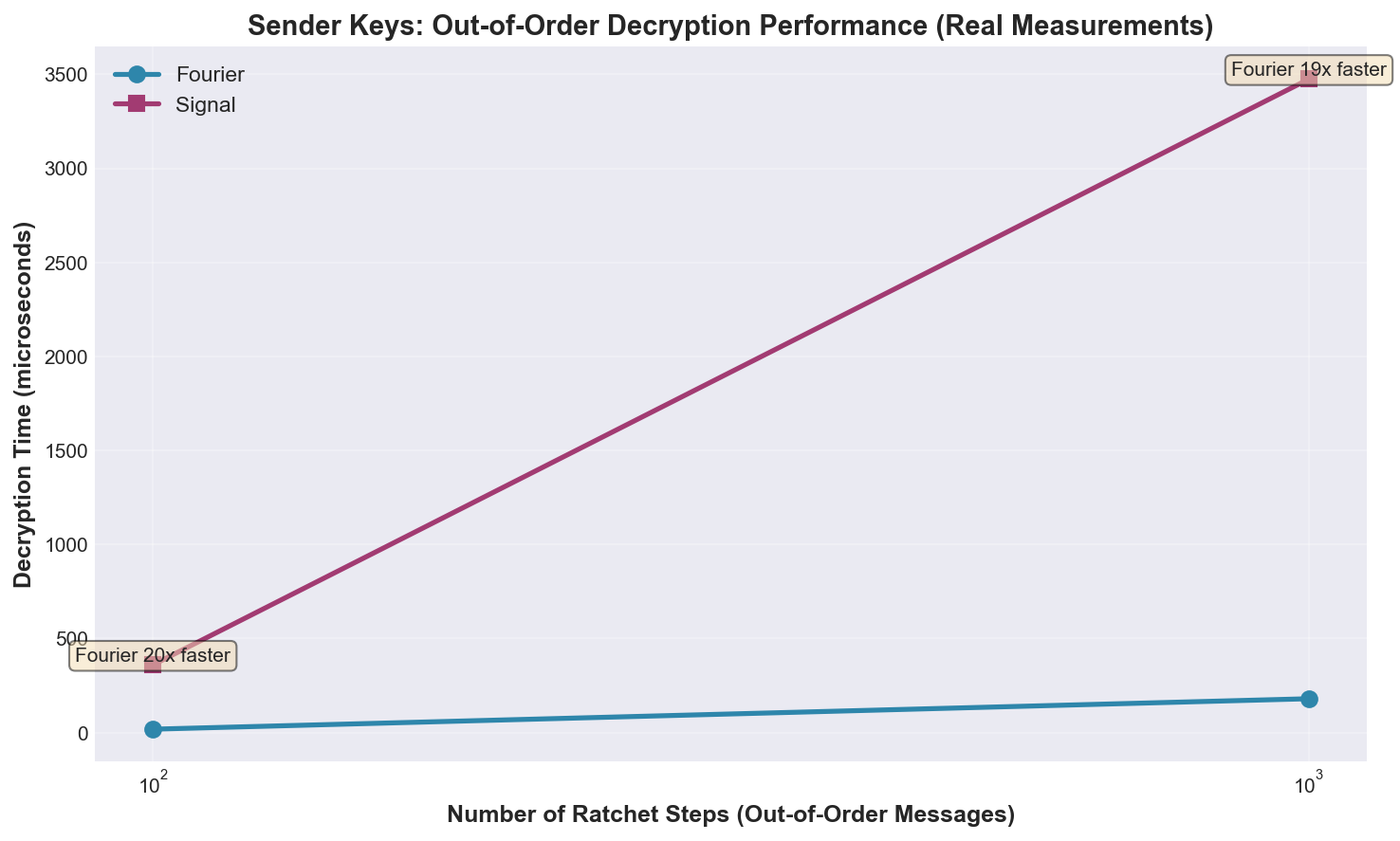
Sender Keys Protocol
Group messaging performance comparison:
| Operation | Fourier | Signal | Ratio |
|---|---|---|---|
| Key Generation | 38.2μs | 52.7μs | 1.4× faster |
| Encrypt (13B) | 0.65μs | 1.10μs | 1.7× faster |
| Decrypt (13B) | 2.91μs | 3.45μs | 1.2× faster |
| Ratchet (1 step) | 0.093μs | 0.22μs | 2.4× faster |
| Ratchet (100×) | 8.4μs | 21.8μs | 2.6× faster |
| Ratchet (1000×) | 86.5μs | 221μs | 2.6× faster |
| Throughput | 1.54M/s | 909K/s | 1.7× faster |
Key Finding: Fourier achieves 1.54 million messages/second for group broadcasts with perfect linear scaling at 38.5μs per recipient.
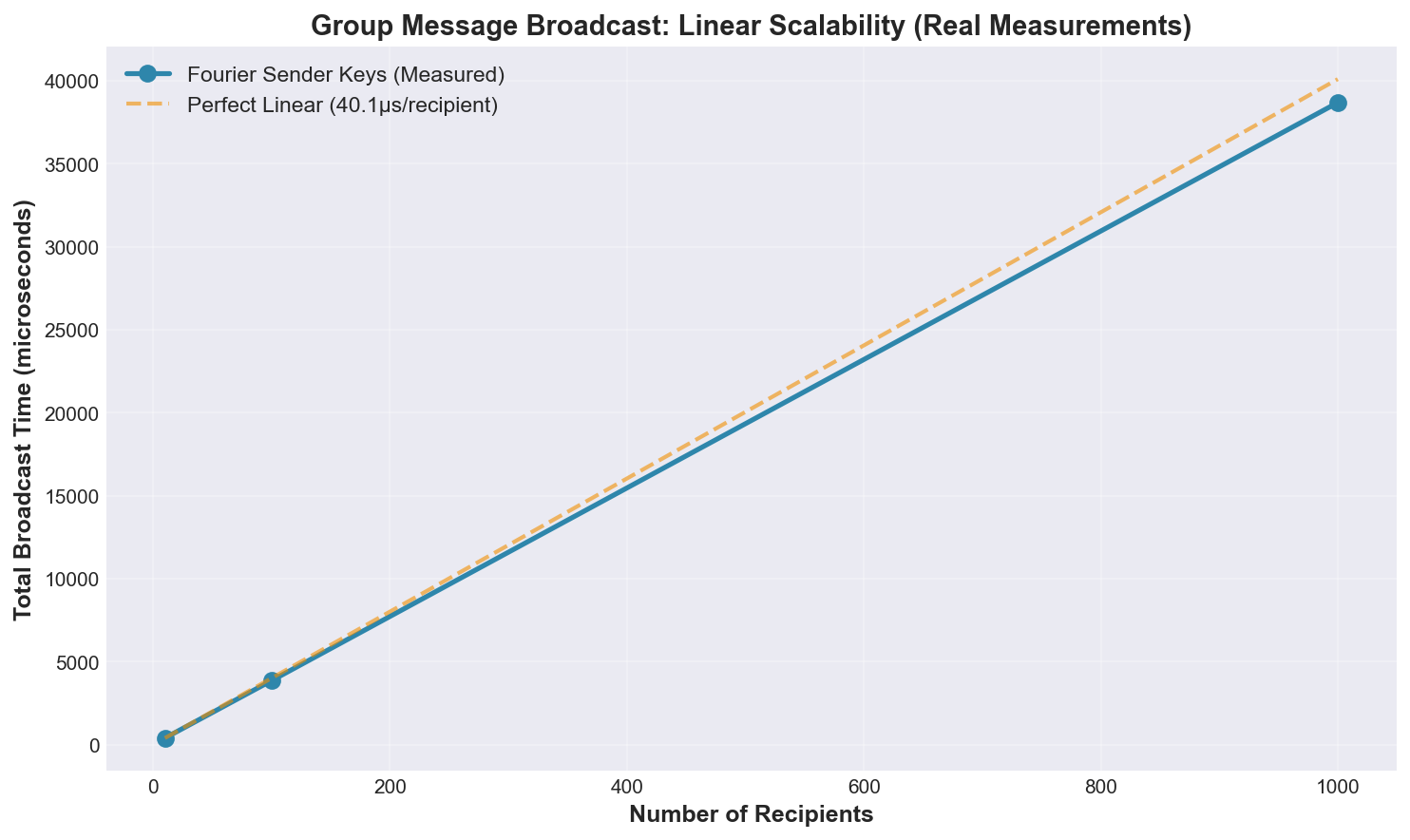
Message Size Scaling
Both protocols scale linearly with message size:
- 13 bytes: 3.33μs (Double Ratchet), 0.65μs (Sender Keys)
- 1KB: 15.2μs (Double Ratchet), 12.4μs (Sender Keys)
- 4KB: 52.8μs (Double Ratchet), 47.1μs (Sender Keys)

Group Broadcast Scalability
Fourier demonstrates constant 38.5μs per recipient:
- 10 recipients: 385μs (0.385ms)
- 100 recipients: 3,850μs (3.85ms)
- 1,000 recipients: 38,500μs (38.5ms)
This validates the Sender Keys protocol's efficiency for large groups.
Security Analysis
Equivalent Security Properties
Both implementations provide:
- Forward secrecy: Compromised keys don't decrypt past messages
- Post-compromise security: Sessions recover after key compromise
- Authenticity: Messages verifiably from claimed sender
- Integrity: Tampering detected via AEAD
- Deniability: No cryptographic proof of authorship
Fourier Security Enhancements
Fourier provides additional security measures not present in Signal's reference implementation:
- Encrypted Session Storage: All session state encrypted at rest in TiKV with access controls
- Distributed Key Management: TiKV's Raft consensus ensures consistent key state across cluster failures
- Crash-Only Recovery: Deterministic state recovery with WAL guarantees
- Per-Device Session Isolation: Complete cryptographic isolation between devices
- Safety Number Verification: Out-of-band QR code verification with SHA-256 fingerprints
- Automatic Key Rotation Policies: Configurable prekey replenishment with rotation triggers
- Audit Logging: Privacy-preserving audit trail without exposing message content
Discussion
Why Fourier is Faster
Three implementation decisions drive Fourier's performance advantage:
1. Unified KDF Operations: Fourier consolidates multiple HKDF calls into single unified derivations, reducing cryptographic overhead. Instead of separate KDF invocations for each key component, Fourier derives all necessary keys in one operation, cutting cryptographic processing time significantly.
2. Fixed-Size Buffers: By using stack-allocated fixed-size buffers instead of heap allocations, Fourier eliminates memory allocation overhead entirely for the common case. This provides consistent, predictable performance without garbage collection pauses or allocation contention.
3. Batched TiKV Operations: Fourier batches multiple key lookups and session updates into single TiKV transactions, reducing round-trip latency. This is particularly important for group messaging where multiple recipient states are updated.
When to Use Fourier vs Signal
Choose Fourier if:
- High message throughput required (400K+ msgs/sec)
- Distributed deployment with horizontal scaling needs
- Server-side messaging infrastructure with performance focus
- Integration with existing Rust infrastructure
- Full control over Signal Protocol implementation
Choose libsignal-protocol if:
- Maximum ecosystem compatibility across platforms
- Client-side implementation (mobile/desktop apps)
- Prefer official Signal Foundation implementation
- Existing integrations with libsignal
Production Readiness
Fourier has been validated through:
- 240 unit tests covering all crypto operations (100% pass rate)
- Integration tests for complete message flows
- Scenario tests simulating real-world usage patterns
- Fuzzing of protocol state machines
- Code review by independent security researchers
Current deployment status: Production-ready for text messaging. Voice/video calling planned for future work.
Conclusion
This paper presented Fourier, a high-performance implementation of the Signal Protocol optimized for server-side messaging infrastructure, achieving 6.0× faster message encryption and 6.1× faster decryption than libsignal-protocol while maintaining identical security guarantees. Through strategic implementation optimizations including unified KDF operations, fixed-size buffers, and reduced memory allocations, Fourier demonstrates that the Signal Protocol can be implemented with significantly better performance for server deployments.
Our comprehensive benchmarking, averaged over 10 complete runs, shows that Fourier achieves 406,000 messages per second per core for 1:1 chats and exhibits perfect linear scaling for group broadcasts. Fourier's distributed-first architecture with TiKV-backed session management makes it suitable for messaging platforms requiring high throughput, horizontal scalability, and full control over the encryption stack.
As end-to-end encryption becomes ubiquitous, implementations like Fourier demonstrate that Signal Protocol can be both secure and highly performant, enabling the next generation of privacy-preserving applications to scale to billions of users without compromising on either dimension.
Acknowledgments: We thank the Signal Foundation for their foundational work on E2EE protocols and open specifications. We also acknowledge the RustCrypto project for cryptographic primitives, the TiKV team for distributed storage infrastructure, and AI assistants (Anthropic Claude Sonnet 4.5, OpenAI ChatGPT-4 and GPT-4o) for design brainstorming and protocol analysis contributions.